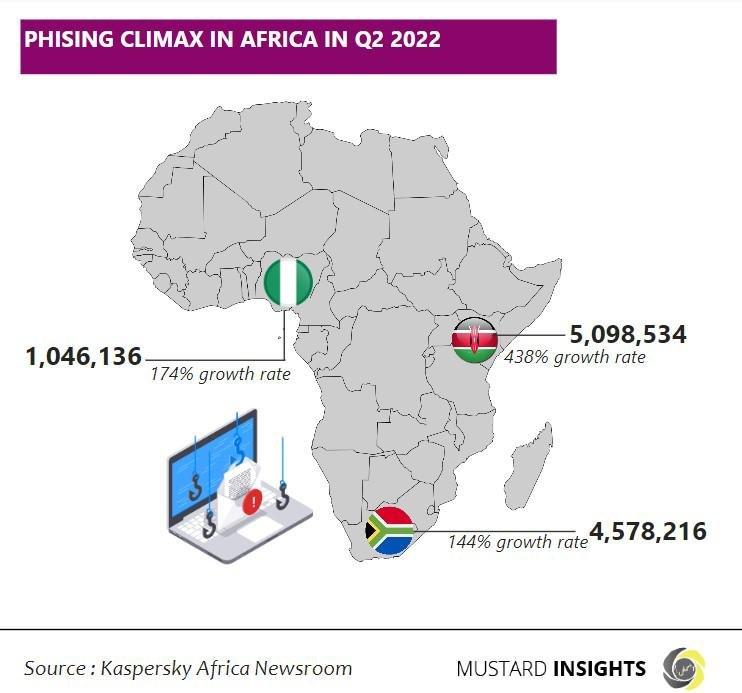
Kenya, South Africa, and Nigeria have emerged as the three African countries with the most phishing attacks in the second quarter of 2022.
Kenya, South Africa, and Nigeria are the three African countries with the most phishing attacks according to research conducted by cybersecurity firm Kaspersky. Analysis of the data revealed that “attacks related to data loss threats (phishing and social engineering scams) increased significantly in Africa in Q2 2022 in comparison with the previous quarter” (Kaspersky).
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables. In cybercrime, these “human hacking” scams tend to lure unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems. Attacks can happen online, in person, and via other interactions (Kaspersky).
According to the KnowBe4 African Report 2019, over “800 respondents across South Africa, Kenya, Nigeria, Ghana, Egypt, Morocco, Mauritius, and Botswana, phishing was one of the top cyber threats faced by the African region. 28.14% of respondents reported that they had previously clicked on a phishing email, 27.71% had previously fallen for a scam, and 19% had forwarded a spam or hoax email”. In 2020 alone Kaspersky detected that South Africa, Kenya, Egypt, Nigeria, Rwanda, and Ethiopia had about 2 million phishing attempts.
Kenya, South Africa and Nigeria Are Countries With The Most Phishing Attacks
Kenya was ranked as the country with the most phishing attacks in Africa with a total of 5,098,534 million phishing attacks recorded - a 438% growth compared to the first quarter of 2022. This comes after reports of cybercrimes in Kenya increased to “nearly 140 million in 2020. Representing an increase of approximately 40 percent in comparison to the previous year, with malware being the most reported online crime in the country” (Statista).
In Kenya, an attack targeted the markets and interconnected cyber systems, with INTERPOL warning that the threat of supply chain attacks may well define the cyber threat landscape over the coming decade. High-profile attacks on supply chains, with the compromise of the Kaseya IT service by the ransomware group REVIL34, are particularly affecting customers in Kenya (Interpol).
South Africa has the second most phishing attacks in Africa with a record number of 4,578,216 million attacks – a 144% growth when compared to the stats from the first quarter of 2022. According to stats from Surfshark, South Africa is ranked sixth among the world’s most affected countries in terms of cybercrime, with an estimated 52 victims per 1 million internet users. In 2021, there were an average of 97 victims per hour, while back in 2001 only 6 South Africans per hour fell victim to cybercrime.”
In South Africa, Life Healthcare, which is the second-largest private hospital operator responsible for administering digital services in hospitals across Southern Africa, was hit by a cyberattack in June 2020. This attack, instigated during the COVID-19 pandemic, affected its admission systems, business processing systems, and email servers, with some systems being forced offline. It is believed to have cost the organization more than a month in downtime during the pandemic (Interpol).”
Nigeria was documented as the third African country with the most phishing attacks, recording 1,046,136 million attacks – a 174% increase when compared to the first quarter. Although Nigeria has the lowest number of attacks amongst the fold, the country seems to have the highest number of scammers present in Africa. A 2020 report from Agari’s Cyber Intelligence Division (ACID) stressed “that a majority (60%) of BEC actors globally were located in Africa, across 11 countries in the region, with “83% percent of African attackers, as well as 50% of global BEC actors, hailing from Nigeria”.
Additionally, “in November 2020 following a joint INTERPOL, Group-IB, and Nigerian Police Force cybercrime investigation, three Nigerian nationals were believed to be members of a wider organized crime group responsible for distributing malware, carrying out phishing campaigns, and extensive BEC scams. The suspects are alleged to have developed phishing links, domains, and mass-mailing campaigns in which they impersonated representatives of organizations. They then used these campaigns to disseminate 26 malware programs, spyware, and remote access tools, including Agent Tesla, Loki, Azorult, Spartan, and the Nanocore and Remcos Remote Access Trojans. These programs were used to infiltrate and monitor the systems of victim organizations and individuals, before launching scams and siphoning funds” (Interpol).
Thoughts?
We won't share your email address. All fields are required.
